Dumpsterdiving for network access
I did a lecture on hardware hacking last year for Tweakers. One of the comments under the announcement was a remark to put my money where my mouth was. Just scaring people by telling them I could simply login to your network when you throw away you broken Smart light was not very credible. And eventhough people were kindly speaking up for me I would still like to illustrate how simple it is.
Step 1 - Breaking a lightbulb⌗
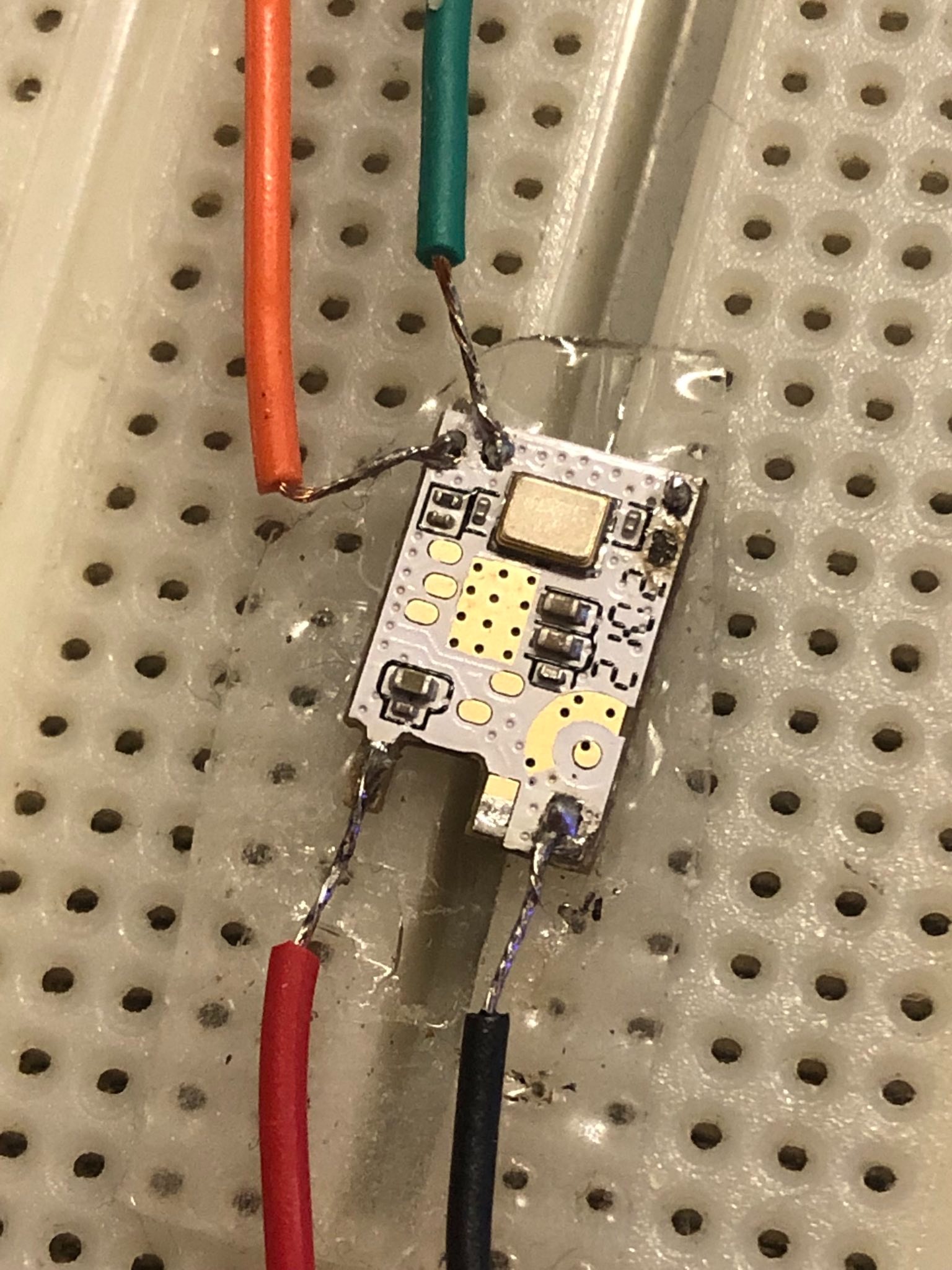
Step 2 - Soldering 4 wires:⌗
 |
 |
|---|
Step 3 - Running 1 script to dump the firmware⌗
jilles@arch ~/tools/tuya_dumps$ ./dump.sh HACK
Connected! Chip info: BK7231S_1.0.5
Reading 4k page at 0X2000000 (0.00%)
Reading 4k page at 0X2001000 (0.20%)
Reading 4k page at 0X2002000 (0.39%)
Reading 4k page at 0X2003000 (0.59%)
| |
| |
Reading 4k page at 0X21FB000 (99.02%)
Reading 4k page at 0X21FC000 (99.22%)
Reading 4k page at 0X21FD000 (99.41%)
Reading 4k page at 0X21FE000 (99.61%)
Reading 4k page at 0X21FF000 (99.80%)
RBL containers:
0x10f9a: bootloader - [encoding_algorithm=NONE, size=0xdd20] - extracted to HACK/HACK_bootloader_1.00.bin
0x129f0a: app - [encoding_algorithm=NONE, size=0xed5e0] - extracted to HACK/HACK_app_1.00.bin
total 3056
-rw-r--r-- 1 jilles jilles 972256 Apr 6 02:40 HACK_app_1.00.bin
-rw-r--r-- 1 jilles jilles 56608 Apr 6 02:40 HACK_bootloader_1.00.bin
-rw-r--r-- 1 jilles jilles 2097152 Apr 6 02:40 HACK.dump
/**< @author <jiewu@bekencorp.com> */
/**< @version v0.3.1 */
encrypt without crc successfully!
-file size: 0xed5f0
/**< @author <jiewu@bekencorp.com> */
/**< @version v0.3.1 */
encrypt without crc successfully!
-file size: 0xdd30
total 4068
drwxr-xr-x 2 jilles jilles 157 Apr 6 02:40 .
drwxr-xr-x 12 jilles jilles 4096 Apr 6 02:39 ..
-rw-r--r-- 1 jilles jilles 972256 Apr 6 02:40 HACK_app_1.00.bin
-rw-r--r-- 1 jilles jilles 972272 Apr 6 02:40 HACK_app_1.00_decrypted.bin
-rw-r--r-- 1 jilles jilles 56608 Apr 6 02:40 HACK_bootloader_1.00.bin
-rw-r--r-- 1 jilles jilles 56624 Apr 6 02:40 HACK_bootloader_1.00_decrypted.bin
-rw-r--r-- 1 jilles jilles 2097152 Apr 6 02:40 HACK.dump
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
52420 0xCCC4 CRC32 polynomial table, little endian
55687 0xD987 Copyright string: "Copyright 1995-2005 Mark Adler "
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
650644 0x9ED94 SHA256 hash constants, little endian
833328 0xCB730 AES Inverse S-Box
846811 0xCEBDB Copyright string: "Copyright (c) 2003-2015, Jouni Malinen <j@w1.fi> and contributors"
889100 0xD910C CRC32 polynomial table, little endian
895777 0xDAB21 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/wifi_sdk/tuya_iot_wifi_api.c
900573 0xDBDDD Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/tuya_cloud/gw_intf.c
907326 0xDD83E Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/tuya_cloud/smart_frame.c
917611 0xE006B Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_base/kv_storge/flash/simple_flash_app.c
920463 0xE0B8F Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_base/sys_serv/uni_time_queue.c
923506 0xE1772 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_adapter/adapter_platform.c
924457 0xE1B29 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_adapter/system/uni_semaphore.c
924977 0xE1D31 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_adapter/utilities/uni_time.c
925485 0xE1F2D Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_adapter/utilities/mem_pool.c
925898 0xE20CA Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_adapter/wifi_intf/wf_basic_intf.c
926044 0xE215C CRC32 polynomial table, little endian
927068 0xE255C CRC32 polynomial table, little endian
928156 0xE299C Base64 standard index table
928486 0xE2AE6 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/bt_conn/tuya_ble_api.c
931060 0xE34F4 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/bt_conn/tuya_ble_mutli_tsf_protocol.c
933576 0xE3EC8 Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/wifi_cfg_serv/ez_mc.c
938044 0xE503C Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/tuya_cloud/iot_httpc.c
943947 0xE674B Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/tuya_cloud/com_protocol.c
955024 0xE9290 SHA256 hash constants, little endian
955549 0xE949D Unix path: /home/share/samba/tuya/wifi_sdk/wifisdk_for_bk7231/project/tuya_iot/src/tuya_iot_sdk/wifi_cfg_serv/wf_sniffer_intf.c
Step 4 - Executing one simple search query⌗
$ strings HACK.dump | grep onveiligwifi -A2
onveiligwifi
61b77bc0c7710cb2e9fe5c8bb4244ed86829789297ba8ee7bf6176de3e6263eb
onveiligwachtwoord
This is all it takes and and depending on the device it would take about 30 minutes⌗
So what should I do?⌗
- Preferably create a seperate network for your IoT devices that is not connected to the rest of your equipment
- Monitor your IoT network for unexpected network devices joining
- Add devices to allow-lists, and remove deprovisioned devices from that list
That sounds like a lot of work, what else can I do?⌗
- Create a new password every time you throw away a broken device
- Open the lightbulb and physically damage all the chips
- Don’t use IoT devices
- Don’t care, get hacked
Read other posts